Identity & Access Management
Identity and Access Management (IAM) is a security framework and set of processes that manage digital identities and control user access to resources. It ensures that only authorised individuals can access the right resources at the right time, preventing unauthorised access and data breaches.
IAM can best be separated into two sides - Authentication and Authorisation. Authentication checks who you are (this happens when you sign into our CPaaS Platform) and Authorisation checks what you are allowed to do once you’re in there. Think of it like going to a concert: authentication is showing your ticket at the entrance to prove you've purchased entry (confirming who you are), while authorisation determines whether you have general admission or VIP backstage access (what you're allowed to do once inside).
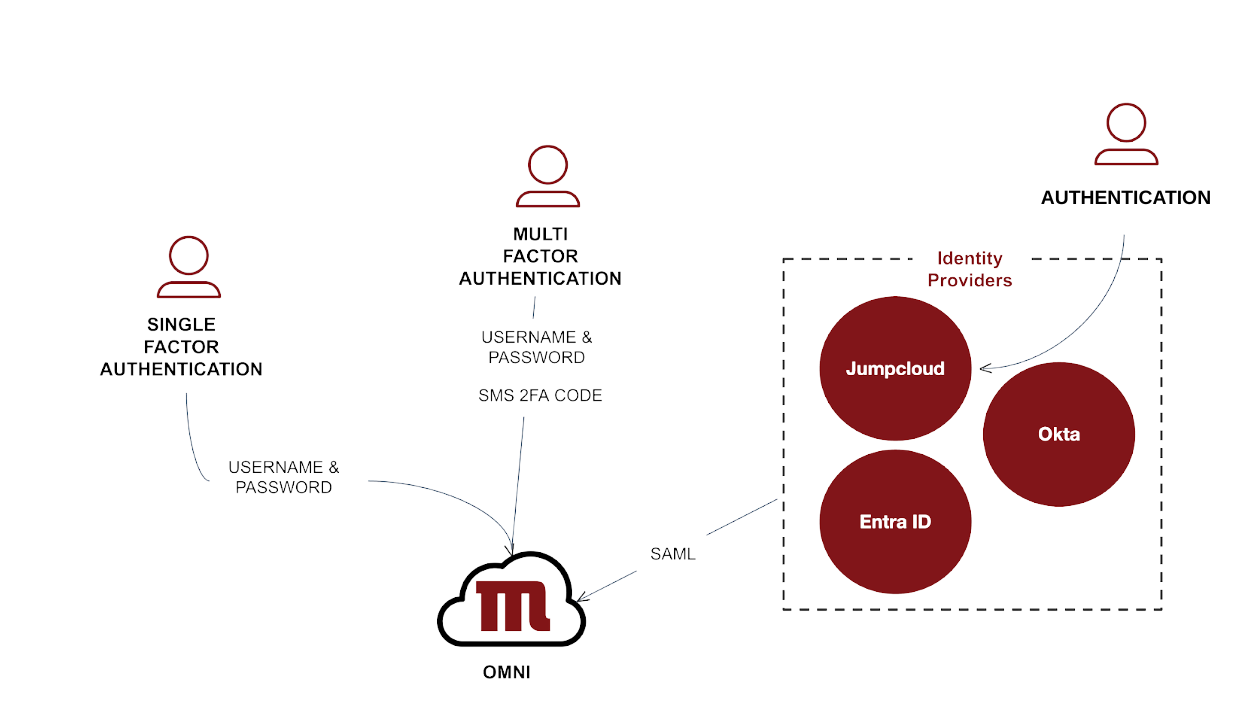
Authentication
There are currently three different ways a customer can sign into our CPaas Platform:SCIM Overview
System for Cross-domain Identity Management (SCIM)
SCIM enables seamless user provisioning directly from your identity provider. When you create, remove, or update user access in platforms like Entra ID, JumpCloud, or Okta, these changes automatically synchronise with our CPaaS Platform, removing duplicate administration.
To enforce access, our CPaaS Platform uses industry-standard Role-Based Access Control (RBAC). This ensures users only see the functions they need, while simplifying permission management for administrators. Permissions govern access to messaging features, reports, and settings. For easier management, administrators can group permissions into roles and assign them to users, with the option to add specific permissions individually when required.
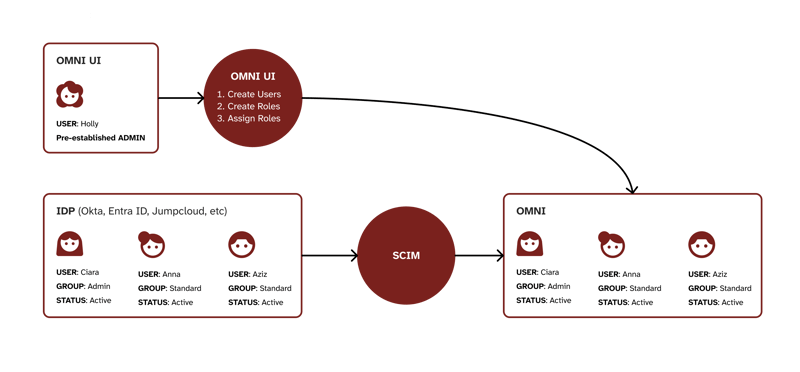
NOTE: An Identity Provider (IdP) is a system that centrally manages user identities and shares authentication information with other applications and services. Examples are: Entra (by Microsoft - most popular), Jumpcloud, Okta and others.